Turn On BitLocker for Windows 11/10 System Drives without TPM
Allowing BitLocker without a TPM will require unlocking the operating system drive at startup with either a password or startup key on a USB flash drive. This option is used when you don’t want to use or have a TPM chip on your PC. 1] Open the Local Group Policy Editor and navigate to this setting-
On the right pane of Operating System Drives double-click Require additional authentication at startup policy to edit it.
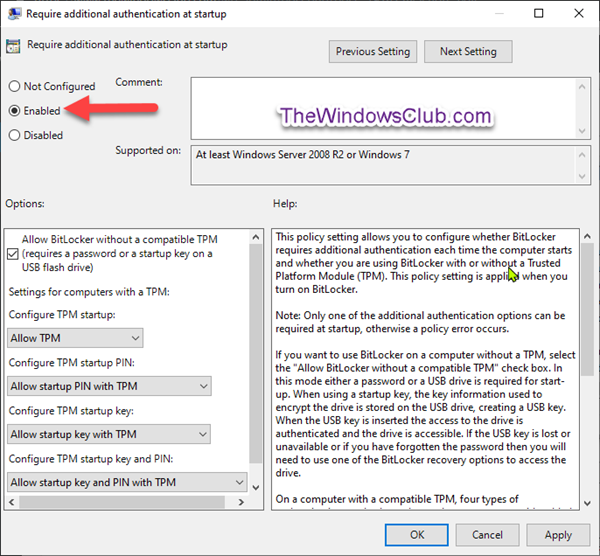
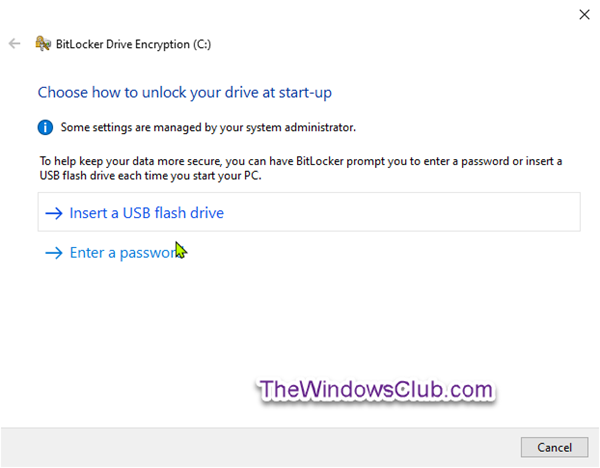
This policy is only applicable to computers running Windows Server 2008 or Windows Vista. On a computer with a compatible Trusted Platform Module (TPM), two authentication methods can be used at startup to provide added protection for encrypted data. When the computer starts, it can require users to insert a USB flash drive containing a startup key. It can also require users to enter a 4-digit to 20-digit startup personal identification number (PIN). A USB flash drive containing a startup key is needed on computers without a compatible TPM. Without a TPM, BitLocker-encrypted data is protected solely by the key material on this USB flash drive. If you enable this policy setting, the wizard will display the page to allow the user to configure advanced startup options for BitLocker. You can further configure setting options for computers with and without a TPM. If you disable or do not configure this policy setting, the BitLocker setup wizard will display basic steps that allow users to turn on BitLocker on computers with a TPM. In this basic wizard, no additional startup key or startup PIN can be configured. Select Enabled at the top, check the Allow BitLocker without a compatible TPM (requires a password or a startup key on a USB flash drive) box under Options. You can now exit Group Policy editor and continue to Step 2 below. 2] Launch File Explorer, right-click the operating system drive that you want to encrypt, and click Turn on BitLocker. Choose how (USB or Password) you want to unlock the operating system drive at startup.
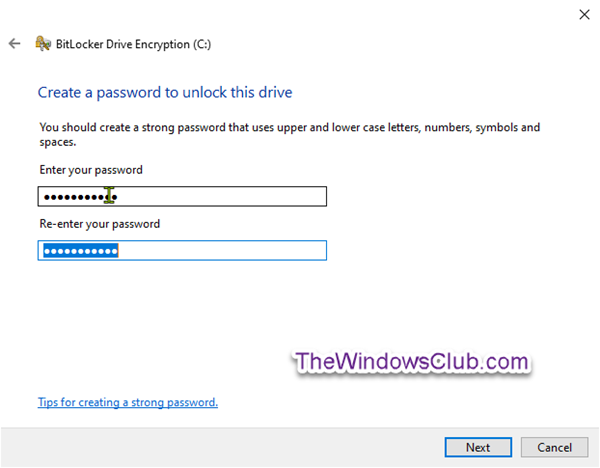
You have two options:
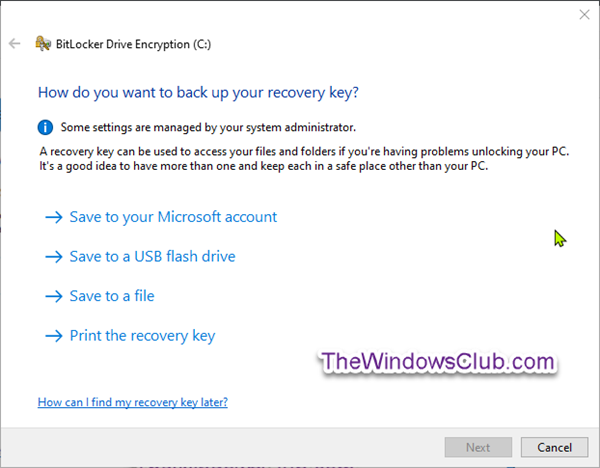
Now, select how (Microsoft account, USB, file, and/or print) you want to back up your BitLocker recovery key for this drive, and click Next.
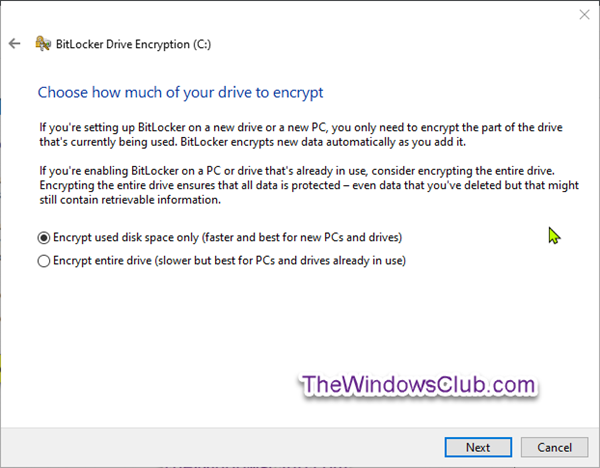
The Microsoft account option is only available when you are signed in to Windows 10 with a Microsoft account. It will save the BitLocker recovery key to your OneDrive account online. Select the radio button for how much of your drive to encrypt (Encrypt entire drive is recommended), and click Next.
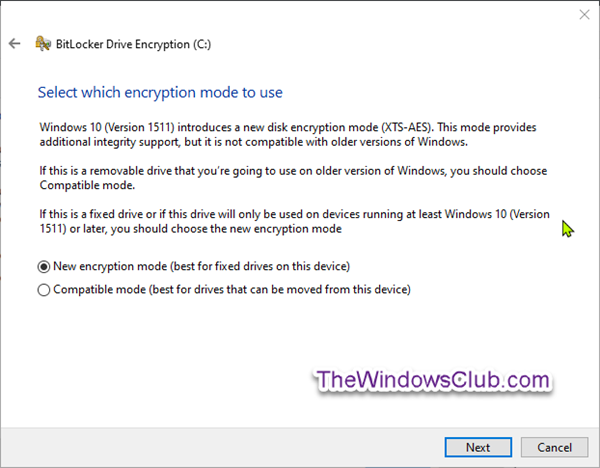
Now, select the radio button for which encryption mode [New encryption mode (XTS-AES 128-bit) or Compatible mode (AES-CBC 128-bit)] to use, and click Next.
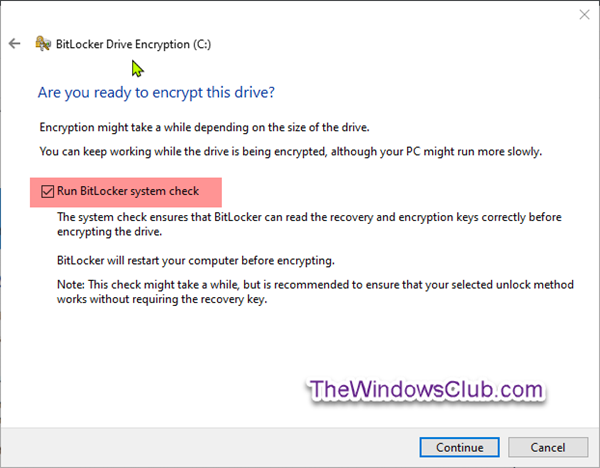
In the next window, uncheck or check (recommended) the Run BitLocker system check box for what you want, and click Continue when ready to start encrypting.
The operating system drive will now start encrypting. When encryption completes, click on Close.
Turn Off BitLocker for Windows System Drives with/without TPM
Whether you encryped your Windows OS drives with a PIN (TPM) or with a password(without TPM), the procedure to decrypt is the same for both cases.
To turn Off BitLocker for Windows 11/10 Operating System Drives
Open an elevated command prompt, type the command below into the elevated command prompt, and hit Enter.
Substitute
Having done this, you can check the status of BitLocker for the drive at any time. Thus you can turn on/off BitLocker for Windows Operating System Drives with/without TPM.